Assess cyber risk faster
and more accurately for any business
CYBERWRITE’S PATENTED TECHNOLOGY
HAS CONSISTENTLY SHOWN A CORRELATION
TO LOWER-THAN-AVERAGE LOSS RATIOs
An immense amount of risk-related data on the internet and in the dark web can provide meaningful cyber insurance insights. But collecting and making sense of this data isn’t something humans can achieve alone in time to positively impact business decisions.
Our pioneering cyber insurance AI orchestration technology, Vivaldi™, enables insurers, reinsurers, brokers, and agents to swiftly and accurately analyze, quantify, and communicate cyber risks to the businesses they serve.
Vivaldi™ brings together the collective power of our years of proprietary historical data, patented 4SEEN® AI algorithm, and diverse AI tools, to deliver cyber insurance risk insights like never before.
Request DemoUnmatched reach, reliability, and accuracy of cyber risk assessments

Superior cyber risk intelligence
Delivers more accurate predictions with thousands of data points about any business and its potential exposure.
- Incorporates more than a decade of data from hundreds of thousands of businesses globally for benchmarking.
- Collects customer-specific risks, industry and geographic risk trends, and business and technology risk indicators – on any business in real time.
- Cross-references data across multiple data points for greater accuracy.
- Continually incorporates data on cyber risk trends, new cyber events, and cyberattacks
ADVANCED AI INCLUDING OUR PATENTED 4SEEN® ALGORITHM
Delivers more accurate predictions with thousands of data points about any business and its potential exposure.
- Conducts millions of simulations to model companies that have had breaches and those that haven’t, identify the underlying patterns, and develop benchmarks.
- Performs detailed cyber risk analyses on potential insureds and compares them to their peers, by size and industry, on key cyber risk factors.
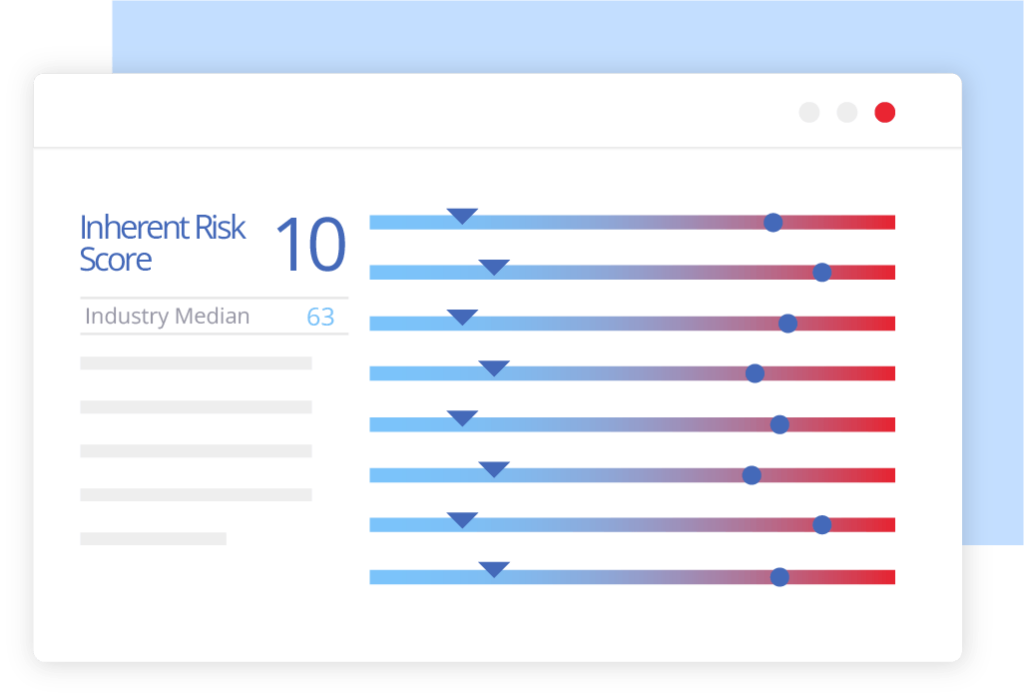
- Predicts each company’s risk of suffering a cyber incident, providing an overall inherent risk score, a risk score for each coverage type, customized for your policy, and the probability of companies with a similar profile to suffer a cyber incident within the next 12 months.
- Augments and contextualizes findings using additional data, such as NIST CVSS framework, to identify the severity of each finding and which cyber risk domains require attention.
Pioneering Financial Impact Analysis
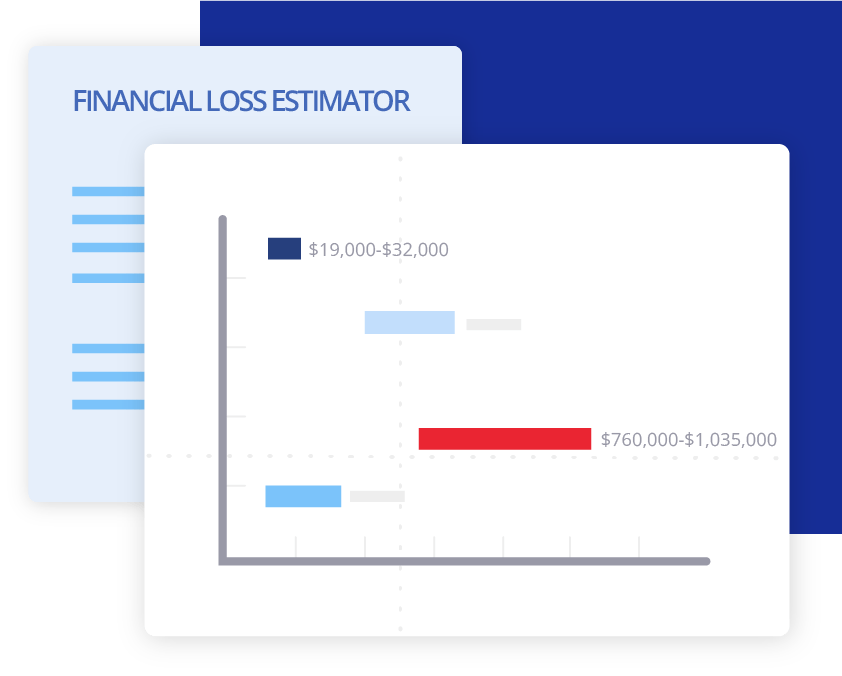
Quantifies the potential cost of a cyberattack for a single business and your entire book of business.
- Conducts AI simulations to predict the cost of a potential breach for any organization.
- Estimates total aggregated financial losses of all potential events on an organization.
- Leverages Cyberwrite 4SEEN® cyber risk score, historical data of past damages to businesses, future regulatory fines, and the costs of managing cyber incidents in its simulations.
- Breaks down losses by coverage type including data compromise, identity recovery, computer attack, cyber extortion, data compromise liability, and more.
- Identifies probable financial losses that would be most likely to occur.
- Request your demo today
Cyberwrite’s Proprietary
cyber risk benchmarking
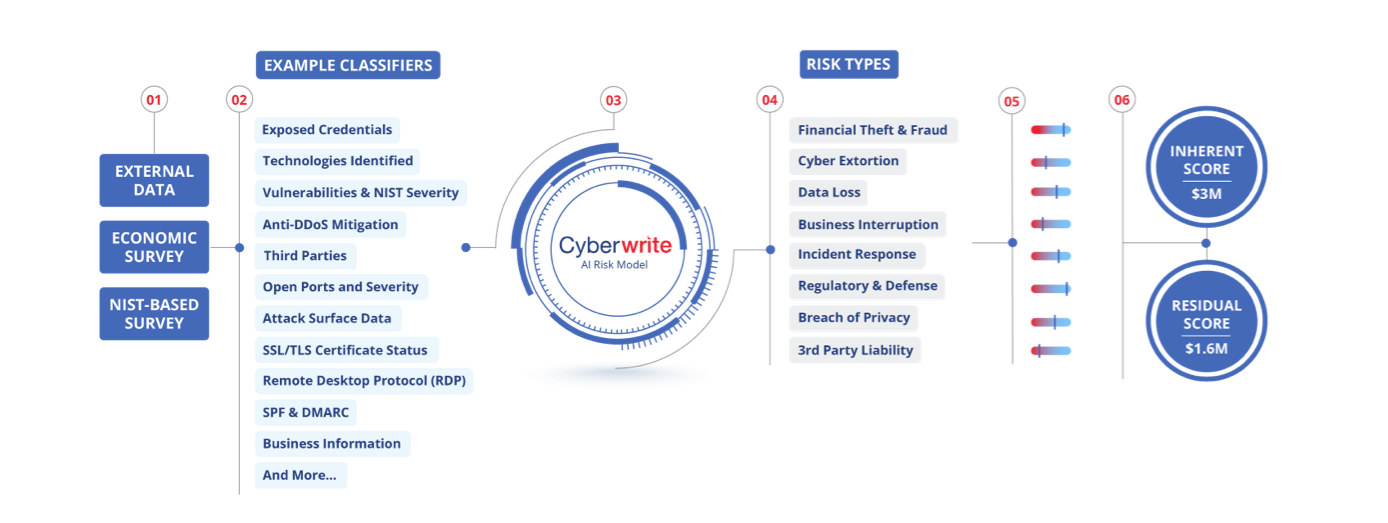
Augment decision-making across the entire cyber insurance lifecycle
Sales
Underwriting
Risk management
Customer engagement